What is CTB Locker or Critroni?
CTB Locker (Curve-Tor-Bitcoin Locker), otherwise known as Critroni, is a file-encrypting ransomware infection that was released in the middle of July 2014 that targets all versions of Windows including Windows XP, Windows Vista, Windows 7, and Windows 8. Just like other file encrypting malware, the media continues to affiliate this infection with CryptoLocker when in fact this appears to have been developed by a different group using new technologies such as elliptical curve cryptography and the malware communicating with the Command and Control server over TOR. As discovered by Kafeine, this malware also appears to be part of a kit being sold online for $3,000 USD, which includes support in getting it up and running. With that said, expect to see other ransomware released using this kit, but possibly with different interfaces. More information on how this malware is being sold can be found in Kafeine's article "Crypto Ransomware" CTB-Locker (Critroni.A) on the rise.
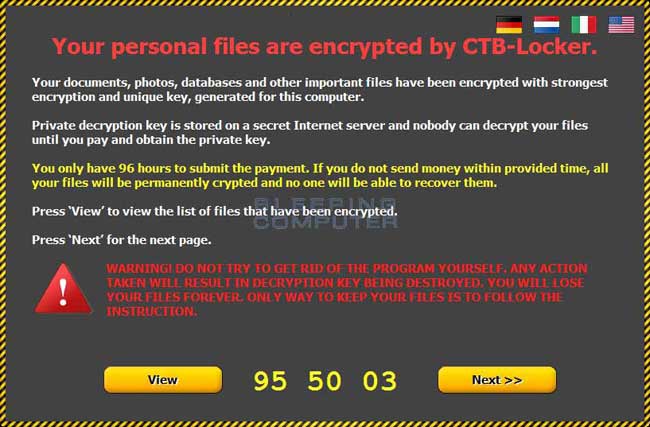
When you are first infected with CTB Locker it will scan your computer for data files and encrypt them so they are no longer accessible. In the past any file that was encrypted would have its file extension changed to CTB or CTB2. The current version now adds a random file extension to encrypted files. The infection will then open a ransom screen that states that your data was encrypted and prompts you to follow the instructions on the screen to learn how to purchase and pay the ransom of .2 BTC. This ransom amount is equivalent to approximately $120.00 USD.
When you become infected with the CTB Locker infection, the malware will store itself in the %Temp% folder as a random named executable. It will then create a hidden random named job in Task Schedule that launches the malware executable every time you login. Once infected the CTB Locker will scan your computer's drives for data files and encrypt them. When the infection is scanning your computer it will scan all drive letters on your computer including mapped drives, removable drives, and mapped network shares. In summary, if there is a drive letter on your computer it will be scanned for data files by CTB Locker.
When CTB Locker detects a supported data file it will encrypt it using elliptical curve cryptography, which is unique to this ransomware infection. When the malware has finished scanning your drives for data files and encrypting them it will display a ransom screen that includes instructions on how to pay the ransom. It will also change your wallpaper to be the %MyDocuments%\AllFilesAreLocked <userid>.bmp file, which contains further instructiosn on how to pay the ransom. Finally it will also create the files %MyDocuments%\DecryptAllFiles <user_id>.txt and
%MyDocuments%\<random>.html that also contain instructions on how to access the malware's site in order to pay the ransom. More information about the ransom site will be discussed later in this guide.
Another uncommon characteristic of this infection is that it will communicate with its Command & Control Server directly via TOR rather than going over the Internet. This technique makes it more difficult, but not impossible, for law enforcement to track down the location of the C2 servers.
Last, but not least, each time you reboot your computer, the malware will copy itself to a new name under the %Temp% folder and then create a new task scheduler job to launch it on login. Therefore, it will not be unusual to find numerous copies of the same executable under different names located in the %Temp% folder.
What are these new extensions like CTBL or CTB2 that are added to the encrypted files?
When you become infected with CTB Locker or Critroni, the infection will encrypt your files and then rename them to a new extension. Older versions of CTB-Locker would change the file extension to .CTBL or .CTB2, while newer ones are using a random extension such as .ftelhdd or .ztswgmc. Therefore, these files are simply your normal data files that have been encrypted. There is no way to open an encrypted file unless you first decrypt it by paying the ransom. If you do attempt to open a file with a program, the program may state that it is corrupted or just display garbled text on the screen. The only way to recover these files so that they show the original, and correct, information is to restore them in some manner or pay the ransom.
What should you do when you discover your computer is infected with CTB Locker
If you discover that your computer is infected with CTB Locker you should immediately scan your computer with an anti-virus or anti-malware program. Unfortunately, most people do not realize CTB Locker is on their computer until it displays the ransom note and your files have already been encrypted. The scans, though, will at least detect and remove the infection from your computer so that it no longer starts when you login to Windows.
To manually remove the infection you would need to remove any executables from the %Temp% folder and then clean the hidden job in the Windows Task Scheduler. This remove the main infection, but will not restore your encrypted files.
New variant of CTB Locker offers free decryption of 5 files.
A new variant of Critroni, aka CTB Locker, now provides the ability to decrypt 5 files as proof that the malware developer can restore your files. At the main decryption screen that pops up on your desktop when you are infected, if you press next you will now be prompted to decrypt 5 files for free.
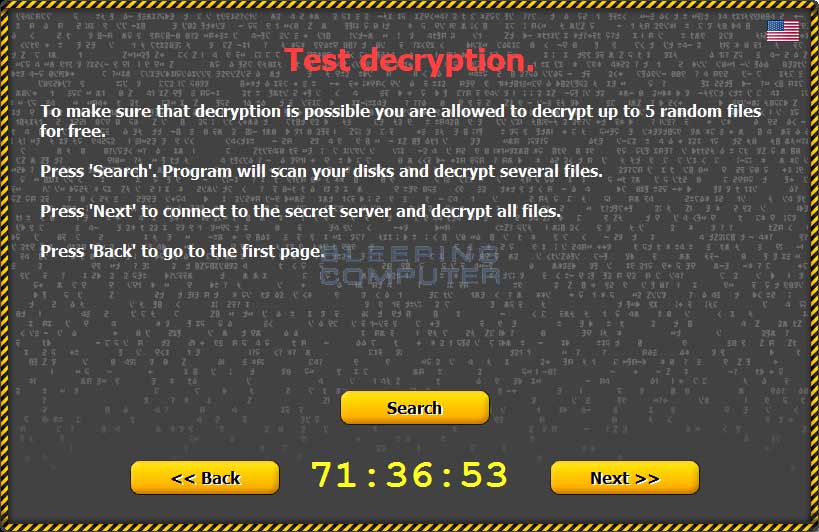
When you click on the search button, it will randomly select 5 encrypted files and then decrypt them for you. This is being done to show proof that paying the ransom will actually enable you to recover your files.
What happens if you do not pay the CTB-Locker ransom in time?
When you are infected with the CTB-Locker ransomware it will state that you have 96 hours to pay the ransom or you will lose your files forever. This is simply a scare tactic and you will still be able to pay the ransom, but will instead need to do it through their TOR site. When the timers counts down to 0, you will be shown a Time expired screen that gives instructions on how to pay the ransom as shown below.
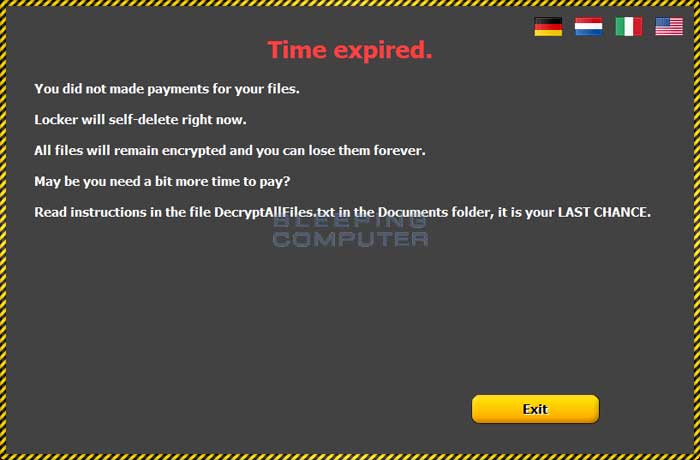
Once you press the Exit button, the program will be closed and the malware file will be deleted. At this point you can open the DecryptAllFiles.txt file found in the Documents folder and follow the instructions there on how to access the CTB-Locker decryption site.
Is it possible to decrypt files encrypted by CTB Locker?
Unfortunately at this time there is no way to retrieve the private key that can be used to decrypt your files without paying the ransom on the CTB Locker Site. Brute forcing the decryption key is not realistic due to the length of time required to break this type of cryptography. Also any decryption tools that have been released by various companies for other malware will not work with this infection. The only methods you have of restoring your files is from a backup, file recovery tools, or if your lucky from Shadow Volume Copies.
How to find files that have been encrypted by CTB Locker
To see a list of files encrypted by this malware you can open the %MyDocuments%\<random>.html or %C:\Users\All Users\<random>.html file. This file not only includes ransom instructions, but also contains a list of the files that have been encrypted by this malware.
CTB Locker and Network Shares
CTB Locker will encrypt data files on network shares only if that network share is mapped as a drive letter on the infected computer. If it is not mapped as a drive letter, then CTB Locker will not encrypt any files on a network share.
It is strongly suggested that you secure all open shares by only allowing writable access to the necessary user groups or authenticated users. This is an important security principle that should be used at all times regardless of infections like CTB Locker.
How to restore files encrypted by CTB Locker
If your files have become encrypted and you are not going to pay the ransom then there are a few methods you can try to restore your files.
Method 1: Backups
The first and best method is to restore your data from a recent backup. If you have been performing backups, then you should use your backups to restore your data.
Method 2: File Recovery Software
It appears that when CTB Locker encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you can may be able to use a file recovery software such as R-Studio or Photorec to recover some of your original files. It is important to note that the more you use your computer after the files are encrypted the more difficult it will be for file recovery programs to recover the deleted un-encrypted files.
Method 3: Shadow Volume Copies
As a last resort, you can try to restore your files via Shadow Volume Copies. Unfortunately, this infection will attempt to delete any Shadow Volume Copies on your computer, but sometimes it fails to do so and you can use them to restore your files. For more information on how to restore your files via Shadow Volume Copies, please see the link below:
How to restore files encrypted by CTB Locker using Shadow Volume Copies
Method 4: Restore DropBox Folders
If you had your dropbox account mapped as a drive letter then it is possible that its contents were encrypted by CTB Locker. If this is the case you can use the link below to learn how to restore your files.
How to restore files that have been encrypted on DropBox folders
How to restore files encrypted by CTB Locker using Shadow Volume Copies
If you had System Restore enabled on the computer, Windows creates shadow copy snapshots that contain copies of your files from that point of time when the system restore snapshot was created. These snapshots may allow us to restore a previous version of our files from before they had been encrypted. This method is not fool proof, though, as even though these files may not be encrypted they also may not be the latest version of the file. Please note that Shadow Volume Copies are only available with Windows XP Service Pack 2, Windows Vista, Windows 7, & Windows 8.
Note: Newer variants of CTB Locker will attempt to delete all shadow copies when you first start any executable on your computer after becoming infected. Thankfully, the infection is not always able to remove the shadow copies, so you should continue to try restoring your files using this method.
In this section we provide two methods that you can use to restore files and folders from the Shadow Volume Copy. The first method is to use native Windows features and the second method is to use a program called Shadow Explorer. It does not hurt to try both and see which methods work better for you.
Using native Windows Previous Versions:
To restore individual files you can right-click on the file, go into Properties, and select the Previous Versions tab. This tab will list all copies of the file that have been stored in a Shadow Volume Copy and the date they were backed up as shown in the image below.
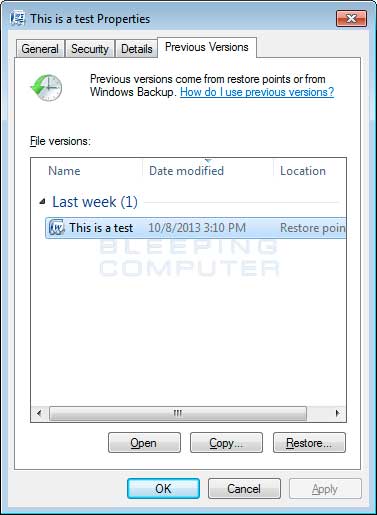
To restore a particular version of the file, simply click on the Copy button and then select the directory you wish to restore the file to. If you wish to restore the selected file and replace the existing one, click on the Restore button. If you wish to view the contents of the actual file, you can click on the Open button to see the contents of the file before you restore it.
This same method can be used to restore an entire folder. Simply right-click on the folder and select Properties and then the Previous Versions tabs. You will then be presented with a similar screen as above where you can either Copy the selected backup of the folder to a new location or Restore it over the existing folder.
Using Shadow Explorer:
You can also use a program called Shadow Explorer to restore entire folders at once. When downloading the program, you can either use the full install download or the portable version as both perform the same functionality.
When you start the program you will be shown a screen listing all the drives and the dates that a shadow copy was created. Select the drive (blue arrow) and date (red arrow) that you wish to restore from. This is shown in the image below.
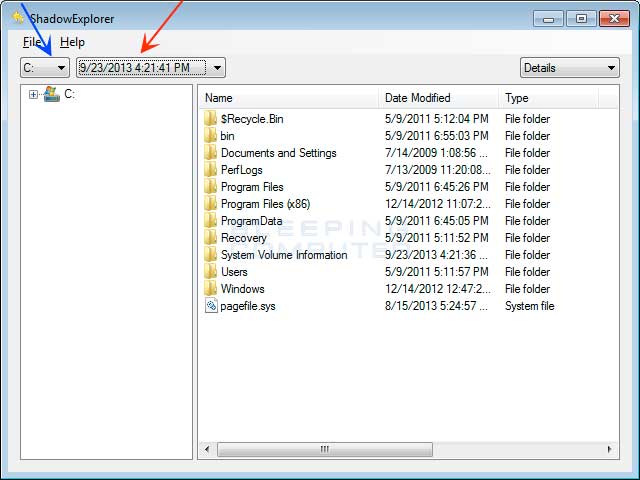
To restore a whole folder, right-click on a folder name and select Export. You will then be prompted as to where you would like to restore the contents of the folder to.
How to restore files that have been encrypted on DropBox folders
If you have DropBox mapped to a drive letter on an infected computer, CTB Locker will attempt to encrypt the files on the drive. DropBox offers free versioning on all of its accounts that will allow you to restore encrypted files through their website. Unfortunately, the restoral process offered by DropBox only allows you to restore one file at a time rather than a whole folder. If you need instructions on restoring an entire folder in DropBox, please click here.
To restore a file, simply login to the DropBox web site and navigate to the folder that contains the encrypted files you wish to restore. Once you are in the folder, right-click on the encrypted file and select Previous Versions as shown in the image below.
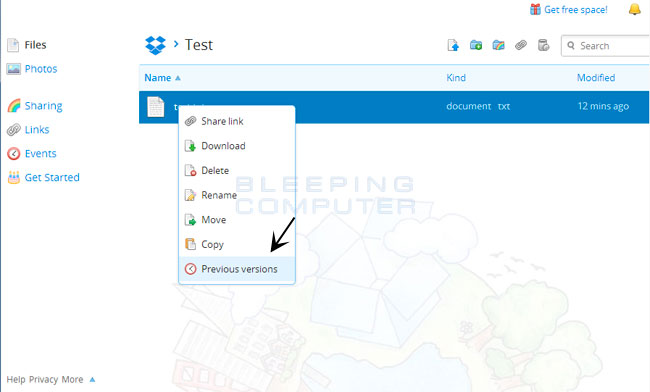
When you click on Previous versions you will be presented with a screen that shows all versions of the encrypted file.
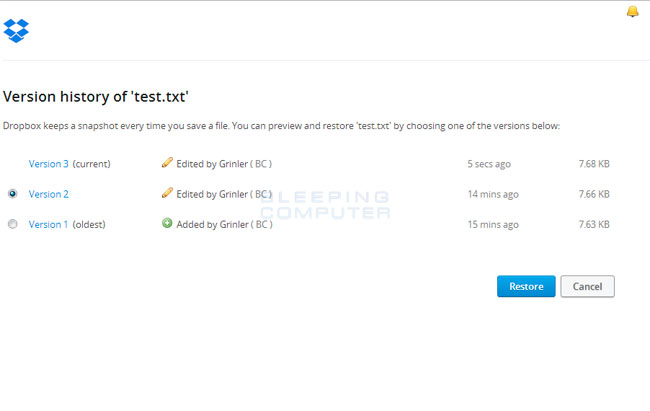
Select the version of the file you wish to restore and click on the Restore button to restore that file.
Unfortunately the process outlined above can be very time consuming if there are many folder to restore. In order to restore an entire folder of encrypted files, you can use the dropbox-restore python script located here. Please note that this script requires Python to be installed on the encrypted computer to execute the script. Instructions on how to use this script can be found in the README.md file for this project.
The CTB Locker Site
The developers of CTB Locker created a TOR web site that victims can use to learn how to pay the ransom to decrypt their files. Links to this site can be found in the %MyDocuments%\AllFilesAreLocked <user_id>.bmp, %MyDocuments%\DecryptAllFiles <user_id>.txt, and %MyDocuments%\<random>.html that are created when you are first infected. At this time the current TOR address is http://zaxseiufetlkwpeu.onion. Once you visit the site you can pay the ransom, which is currently $120 USD by sending Bitcoins to the specified address. This bitcoin address will be unique to your computer and will not be used by others.
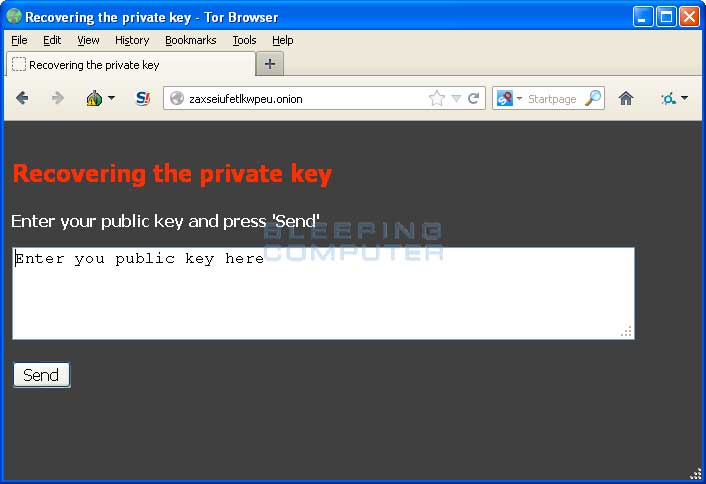
Once a payment is made you must wait until there are a certain amount of bitcoin confirmations before your private key and a decrypter will supposedly be made available for download. At this time the infection is too new to know if paying the ransom will actually get you a decryption tool.
Will paying the ransom actually decrypt your files?
At this point the infection is too new to know the answer to this question. As we learn more, we will update this FAQ to contain this information.
How to prevent your computer from becoming infected by CTB Locker
You can use the Windows Group or Local Policy Editor to create Software Restriction Policies that block executables from running when they are located in specific paths. For more information on how to configure Software Restriction Policies, please see these articles from MS:
http://support.microsoft.com/kb/310791
http://technet.microsoft.com/en-us/library/cc786941(v=ws.10).aspx
The file paths that have been used by this infection, and others, are:
C:\<random>\<random>.exe
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Users\<User>\AppData\Local\<random>.exe (Vista/7/8)
C:\Documents and Settings\<User>\Application Data\<random>.exe (XP)
C:\Documents and Settings\<User>\Local Application Data\<random>.exe (XP)
%Temp%
In order to block the CTB Locker you want to create Path Rules so that they are not allowed to execute. To create these Software Restriction Policies, you can either use the CryptoPrevent tool or add the policies manually. Both methods are described below.
How to use the CryptoPrevent Tool:
FoolishIT LLC was kind enough to create a free utility called CryptoPrevent that automatically adds the suggested Software Restriction Policy Path Rules listed below to your computer. This makes it very easy for anyone using Windows XP SP 2 and above to quickly add the Software Restriction Policies to your computer in order to prevent CTB Locker and Zbot from being executed in the first place.
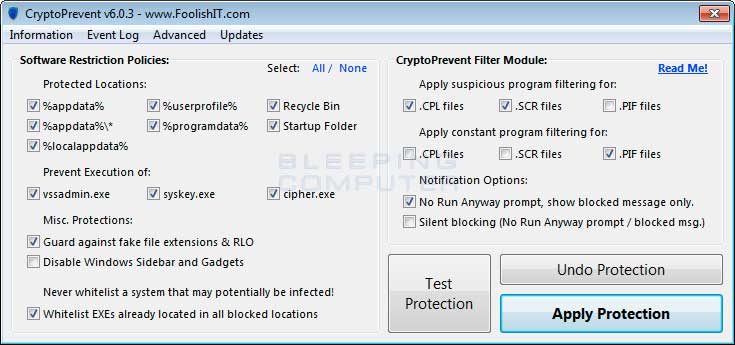
A new feature of CryptoPrevent is the option to whitelist any existing programs in %AppData% or %LocalAppData%. This is a useful feature as it will make sure the restrictions that are put in place do not affect legitimate applications that are already installed on your computer. To use this feature make sure you check the option labeled Whitelist EXEs already located in %appdata% / %localappdata% before you press the Block button.
You can download CryptoPrevent from the following page:
http://www.foolishit.com/download/cryptoprevent/
For more information on how to use the tool, please see this page:
http://www.foolishit.com/vb6-projects/cryptoprevent/
Once you run the program, simply click on the Apply Protection button to add the default Software Restriction Policies to your computer. If you wish to customize the settings, then please review the checkboxes and change them as necessary. If CryptoPrevent causes issues running legitimate applications, then please see this section on how to enable specific applications. You can also remove the Software Restriction Policies that were added by clicking on the Undo button.
How to manually create Software Restriction Policies to block CTB Locker:
To manually create Software Restriction Policies you need to do it within the Local Security Policy Editor or Group Policy Editor. If you are a home user you should create these policies using the Local Security Policy editor. If you are on a domain, then your domain administrator should use the Group Policy Editor. To open the Local Security Policy editor, click on the Start button and type Local Security Policy and select the search result that appears. You can open the Group Policy Editor by typing Group Policy instead. In this guide we will use the Local Security Policy Editor in our examples.
Once you open the Local Security Policy Editor, you will see a screen similar to the one below.
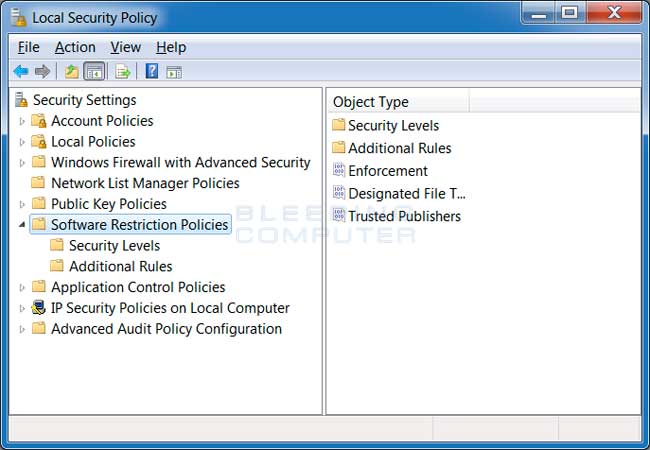
Once the above screen is open, expand Security Settings and then click on the Software Restriction Policies section. If you do not see the items in the right pane as shown above, you will need to add a new policy. To do this click on the Action button and select New Software Restriction Policies. This will then enable the policy and the right pane will appear as in the image above. You should then click on the Additional Rules category and then right-click in the right pane and select New Path Rule.... You should then add a Path Rule for each of the items listed below.
If the Software Restriction Policies cause issues when trying to run legitimate applications, you should see this section on how to enable specific applications.
Below are a few Path Rules that are suggested you use to not only block the infections from running, but also to block attachments from being executed when opened in an e-mail client.
Block CTB Locker executable in %AppData%
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.
Block CTB Locker executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from %AppData%.
Block Zbot executable in %AppData%
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from immediate subfolders of %AppData%.
Block Zbot executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*\*.exe
Security Level: Disallowed
Description: Don't allow executables to run from immediate subfolders of %AppData%.
Block executables run from archive attachments opened with WinRAR:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\Rar*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\Rar*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.
Block executables run from archive attachments opened with 7zip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\7z*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\7z*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7zip.
Block executables run from archive attachments opened with WinZip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\wz*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\wz*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.
Block executables run from archive attachments opened using Windows built-in Zip support:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\*.zip\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\*.zip\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened using Windows built-in Zip support.
You can see an event log entry and alert showing an executable being blocked:
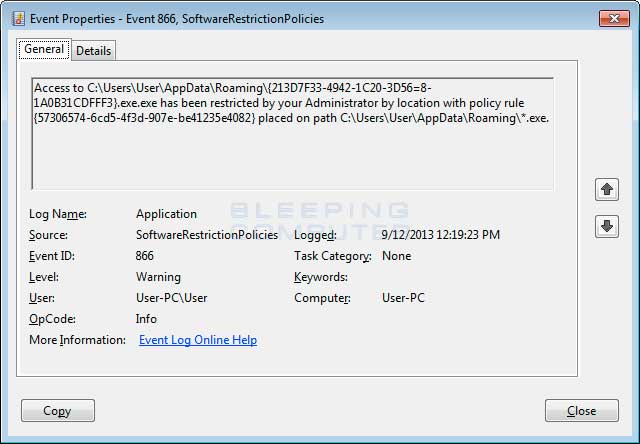
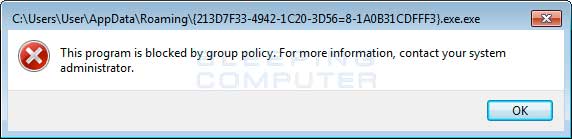
If you need help configuring this, feel free to ask in the CTB Locker help topic.
How to allow specific applications to run when using Software Restriction Policies
If you use Software Restriction Policies, or CryptoPrevent, to block CTB Locker you may find that some legitimate applications no longer run. This is because some companies mistakenly install their applications under a user's profile rather than in the Program Files folder where they belong. Due to this, the Software Restriction Policies will prevent those applications from running.
Thankfully, when Microsoft designed Software Restriction Policies they made it so a Path Rule that specifies a program is allowed to run overrides any path rules that may block it. Therefore, if a Software Restriction Policy is blocking a legitimate program, you will need to use the manual steps given above to add a Path Rule that allows the program to run. To do this you will need to create a Path Rule for a particular program's executable and set the Security Level to Unrestricted instead of Disallowed as shown in the image below.
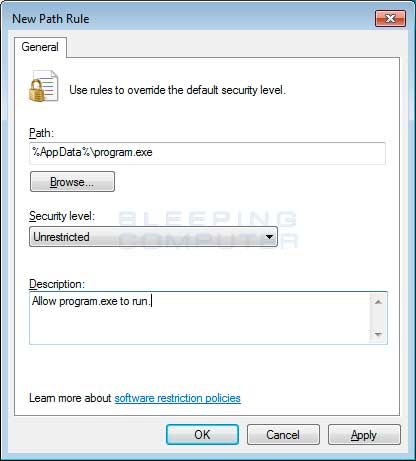
Once you add these Unrestricted Path Rules, the specified applications will be allowed to run again.
Critroni time line and updates
Below is a time line of the Critroni or CTB Locker infection and its various updates:
Middle of July 2014 The Critroni infection was introduced for the first time.
8/27/14 A new variant of Critroni was released that includes free decryption of 5 files and changes the extension of encrypted files to CTB2.
12/10/14 New variant that uses random file extensions for the encrypted files. Examples of a new random file extension is .ztswgmc.
1/20/15 New variant adds new language localization options in the malware program. CTB-Locker now has localized text in German, Italian, Dutch, and English. This variant also extends the ransom timer to 96 hours.
Threat Classification:
Information on Ransomware Programs
Advanced information:
View CTB Locker files.
View CTB Locker Registry Information.
Guide Updates:
07/28/14 - Initial guide creation
07/31/14 - Added info about CTBL files.
08/28/14 - Updated for new variant that includes free decryption of 5 files and changes extension to CTB2.
12/10/14 - New variant uses random extensions for encrypted files.
1/20/15 - Updated for new variant that contains more language localizations.
1/29/15 - Added information on what happens when you do not pay the ransom by the deadline.
Article source : bleepingcomputer.com
© 2011-2024 All rights reserved